
Table of Contents
1. Introduction
In today’s industrial world, data drives decision-making, compliance, and innovation. As organizations expand Industry 4.0 initiatives, predictive maintenance, and AI insights, one challenge remains: Can you trust your data — continuously, at scale, and under regulatory scrutiny?
xLM, in partnership with Sentra, introduces a new paradigm: Continuous Data Integrity Posture Management (cDIPM).
2. Why cDIPM now?
Traditional data governance and one-off audits no longer suffice. Data streams in real time from sensors, SCADA systems, cloud platforms, and AI pipelines. Risks like drift, misclassification, or unauthorized access can harm operations, compliance, and business outcomes.
With cDIPM, xLM combines its Continuous Intelligence portfolio and Sentra’s DSPM capabilities to provide a continuously validated, proactive, and auditable data integrity framework. This is a core operating layer for trusted industrial data.
ALCOA+ principles at the core:
Attributable — link every dataset to its generator.
Legible — record data in permanent, clear formats.
Contemporaneous — capture data at the time of generation.
Original — preserve source records or certified true copies.
Accurate — validate and verify at every stage.
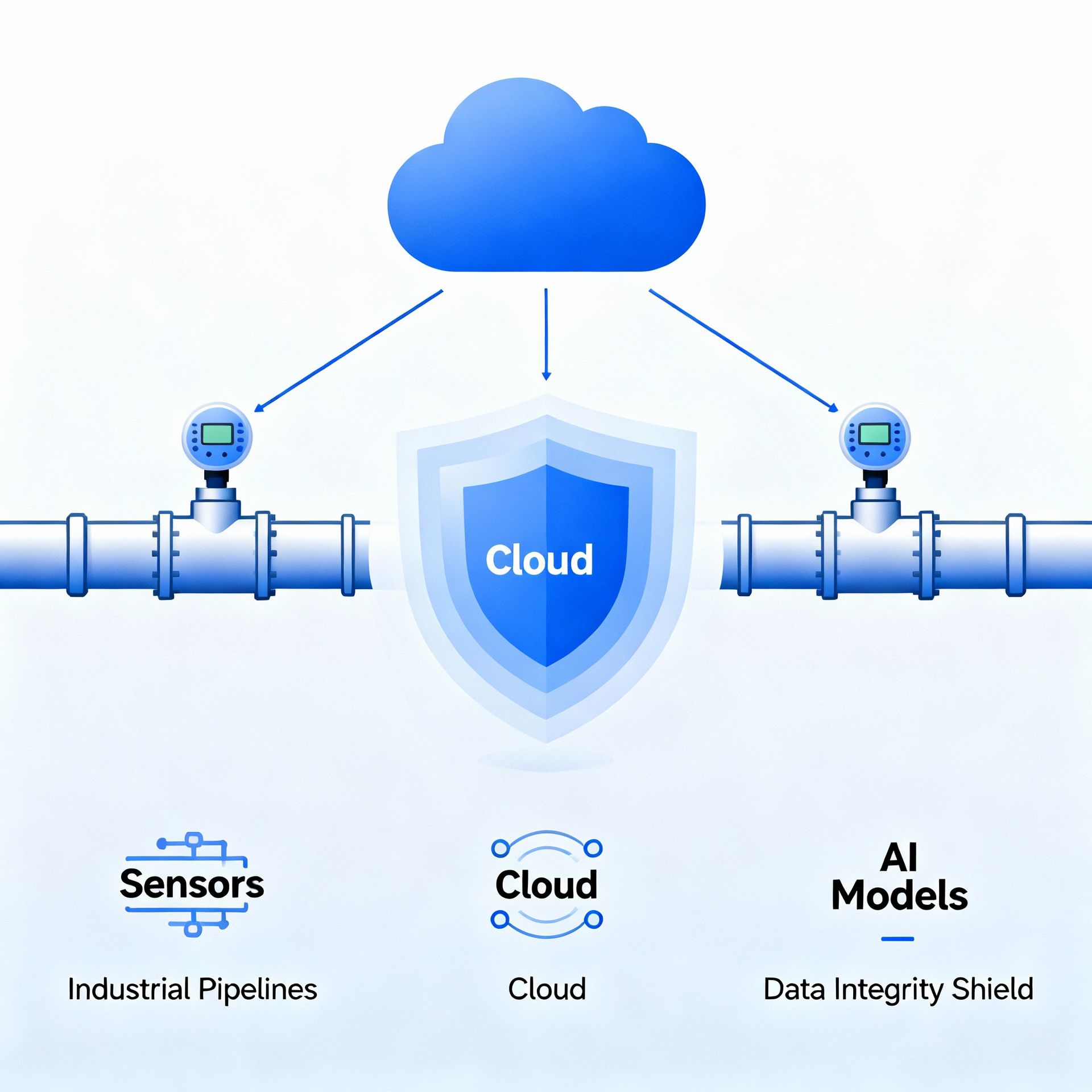
Complementing ALCOA+, cDIPM enforces Complete, Consistent, Enduring, and Available data throughout its lifecycle.
3. What is continuous data integrity posture management (cDIPM)?
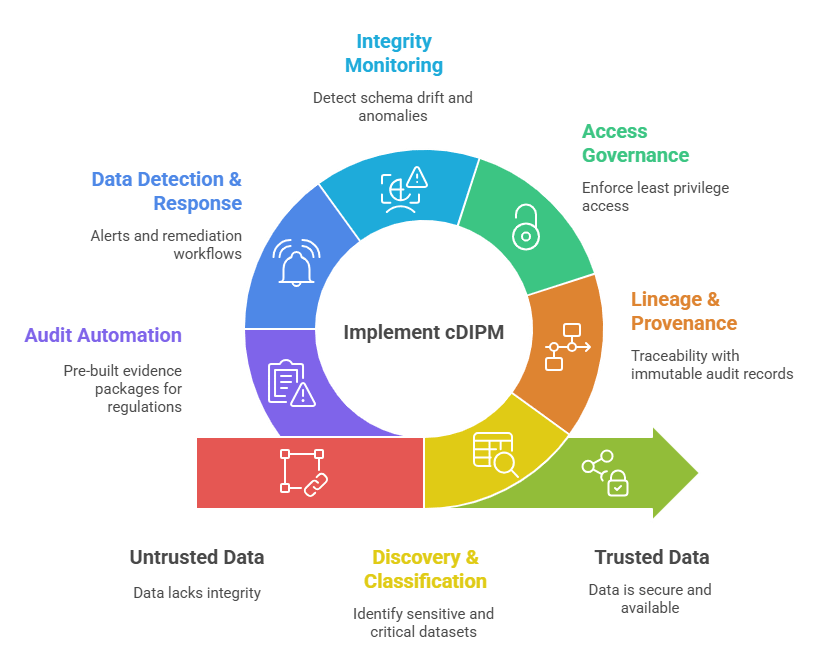
cDIPM is an operational framework that continuously ensures the integrity, provenance, security, and availability of industrial and enterprise data.
It embeds continuous validation loops into data pipelines, ensuring every dataset, model input, and analytic output is trustworthy.
Key pillars include:
Discovery & classification — auto-identify sensitive and critical datasets across OT, IT, and cloud.
Lineage & provenance — end-to-end traceability with immutable audit records.
Access governance — enforce least privilege and detect permission drift in real time.
Integrity monitoring — detect schema drift, validate checksums, and monitor anomalies in streaming data.
Data detection & response (DDR) — instant alerts and remediation for suspicious access or exfiltration.
Audit automation — pre-built evidence packages aligned with regulations like GxP, FDA 21 CFR Part 11, GDPR, HIPAA.
Unlike conventional tools, cDIPM operates in real time and is self-reinforcing: the more data it validates, the smarter its controls and classifiers become.
4. Deploying the cDIPM foundation
Start by deploying a validated instance, providing discovery, classification, and continuous monitoring. This establishes data security, lineage, and access requirements from the start.
Key features powering cDIPM:
Agentless Scanning — non-intrusive, scalable scans across OT, IT, and cloud.
AI-Enhanced Classification — context-aware classification of PII, PHI, and regulated manufacturing data.
Risk & Threat Mitigation — proactive detection of exposure risks, misconfigurations, and shadow datasets.
Data Loss Prevention (DLP) — real-time policies preventing unauthorized movement of validated data.
Data Access Governance — enforce least privilege to maintain attributability and availability.
Data Catalog Fidelity — centralized catalog with classification, lineage, and validation metadata.
Continuous Monitoring & Drift Detection — real-time validation ensures datasets remain accurate, consistent, and enduring.

Once deployed, cDIPM ensures the data integrity of OT, IT, and cloud datasets. It automatically detects drift, and “validated datasets” feed xLM’s ContinuousOS apps. Continuous Intelligent Validation (cIV) keeps cDIPM in a validated state — always inspection-ready.
5. How cDIPM works in practice
Consider a predictive maintenance model monitoring turbine health:
Sensors stream telemetry (temperature, vibration, RPM) into cloud storage.
cDIPM validates incoming data for completeness, schema conformity, and checksum integrity.
Lineage mapping lets analysts trace every model input to its source timestamp.
If a permission misconfiguration exposes raw data, DDR triggers automatic remediation — revoking access and alerting the steward.
During an audit, compliance teams export immutable evidence in minutes, not weeks.
This means the model predicts remaining useful life (RUL) using validated, compliant, and trustworthy data.

6. Benefits for regulated industries
With cDIPM, organizations gain:
Regulatory confidence — compliance-by-design with GxP, FDA 21 CFR Part 11, Annex 11
Operational resilience — reduced downtime by detecting drift and anomalies early.
Faster audits — pre-packaged, tamper-evident evidence delivered in hours.
Secure innovation — safely scale AI, digital twins, and decision intelligence.
For regulated sectors like life sciences, cDIPM accelerates compliance and trust.

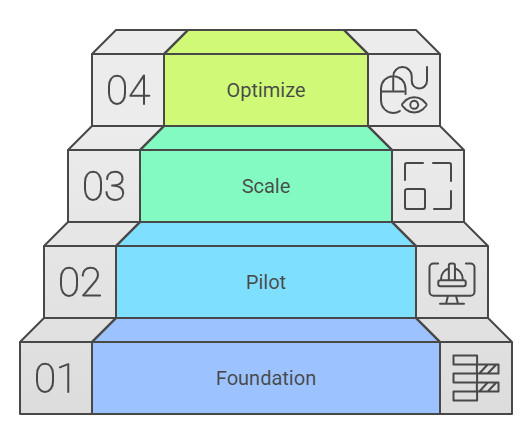
7. Roadmap to adoption
xLM’s cDIPM rollout with Sentra follows a clear path:
Phase 1 (Foundation): Connect critical data sources, baseline integrity, assign data owners.
Phase 2 (Pilot): Enable monitoring and DDR for one predictive maintenance model.
Phase 3 (Scale): Extend across cloud and OT pipelines, integrate IAM and SIEM/SOAR systems.
Phase 4 (Optimize): Automate remediation playbooks, track KPIs like MTTD and audit readiness.
This roadmap helps enterprises achieve continuous compliance readiness, reduce downtime, and scale AI safely.
8. Call-to-action
Continuous Data Integrity Posture Management (cDIPM) is more than a framework — it enforces ALCOA+ at scale, continuously. Powered by xLM and Sentra, it turns compliance, resilience, and trust into competitive advantage.
If your organization is ready to embed data integrity into every decision, now is the time to adopt cDIPM.

