
Table of Contents
Are your Manufacturing IT assets protected by state of the art Cybersecurity?
Industry 4.0 and "smart factories" are transforming the manufacturing industry. As drug and device manufacturers embrace digital transformation and IT/OT convergence, they are expanding their attack surface and increasing their risk of vulnerability exploitation, production sabotage, IP leakage, and other security issues. With such inherent vulnerabilities, GxP companies cannot comply with the FDA’s Data Integrity mandates.
xLM has partnered with Sophos to deliver Cybersecurity-as-a-Service backed by security specialists that monitor your IT environment 24/7/365. We detect and respond to cyberattacks targeting manufacturers' servers, industrial control systems, networks, cloud workloads, email accounts, and more. Our ContinuousMTR Cybersecurity-as-a-Service is geared to protect your company’s IT assets so that your business risk exposure is reduced while data integrity compliance is increased.
What can ContinuousMTR do?
Stop Ransomware Attacks and Data Breaches
ContinuousMTR Managed Detection and Response (MDR) is a fully managed 24/7/365 service delivered by experts that detect and respond to sophisticated cyberattacks that technology solutions alone cannot prevent.
ContinuousMTR meets you where you are. It's compatible with:
Your existing security investments – we can use tools, third-party tools, or any combination of the two
Your needs – whether you want full-scale incident response or help making accurate security decisions, we've got you covered
Your industry – MDR secures hundreds of manufacturing organizations worldwide; we understand the industry's threats and are building "community immunity"
Secure Access to Your Critical Industrial Control Systems and Data
Lifescience companies need to adopt a zero-trust approach of "trust nothing, verify everything" to secure access to their critical infrastructure and proprietary information.
The Zero Trust Network Access (ZTNA) solution continuously validates user identity, device health, and compliance before granting access to your applications and data.
Endpoint and ZTNA work together to share status and health information to automatically prevent compromised hosts from connecting to your networked resources. They also prevent threats from moving laterally across your organization and getting a foothold on your network.
Our Secure Access portfolio allows you to connect your remote devices and branch offices, deliver critical cloud and SaaS applications, and securely share data.
It includes ZTNA to secure access to your applications, SD-RED remote Ethernet devices to safely extend your network to your remote devices and branch offices, Wireless access points for easy and secure wireless networking, and Switch network access layer switches for secure access on the LAN. Everything is managed through Central, which is an all-in-one cloud-based security platform.
Ensure Uninterrupted Availability Across Your Manufacturing Operations
Proactively detect malicious behaviors on your hosts with intelligent threat protection from Intercept X, which combines deep learning, host intrusion prevention system (HIPS), anti-exploit, anti-adversary, and malicious traffic detection capabilities.
Get protection that constantly learns and improves with the Adaptive Cybersecurity Ecosystem (ACE), which enables various products to work together and automatically respond to threats and stop and clean them up in seconds.
See the full cybersecurity picture with Extended Detection and Response (XDR), which integrates multiple data sources to give you a holistic view of your organization's cybersecurity environment and drills down into granular detail as needed.
Get emergency support with active threats. Our team with our partner Sophos will help you quickly control an attack to protect your networks, applications, and data and mitigate damage and disruption.
Identify risky users based on their recent web activity and threat and infection history so you can take appropriate action. A user's risk score can help you detect unintentional actions due to a lack of security awareness or a rogue or negligent user.
Protect Against Insider Attacks
Threats like exfiltration of proprietary data and modification of critical system data and processes can be catastrophic to drug and device manufacturers. ContinuousMTR helps you stop insider attacks and reduce risk across your organization.
User-Based Access and Controls
Promote user awareness across all areas of the firewall and user-based policy controls across your applications, websites, traffic shaping (QoS), and other network resources, regardless of the IP address, location, network, or device.
User Risk Visibility
User Threat Quotient (UTQ) provides actionable intelligence on user behaviors, with insights into the riskiest users and applications to ensure that your policies are enforced before your security is compromised.
Data Loss Prevention
Protect your sensitive data from accidental or malicious disclosure with complete policy control over your web categories, applications, removable media, and mobile devices.
Minimize the Risk of Supply Chain Attacks
Manufacturing supply chains are vast and complex. A vulnerability in any of a supplier’s networks can rapidly propagate to infect multiple suppliers and businesses. Our partner Sophos provides security technologies and services to mitigate the risk of supply chain attacks.
Intercept X with XDR
Use AI, anti-ransomware and other advanced technologies to defend against threats that can infiltrate your network via third-party suppliers. Plus, XDR functionality enables you to automatically identify suspicious activities, prioritize threat indicators, and quickly search for potential threats across your endpoints and servers.
Managed Detection and Response (MDR)
Get 24/7/365 expert support with over 500 Sophos specialists working around the clock to proactively hunt for, validate, and remediate potential supply chain threats and incidents on your behalf.
Zero Trust Network Access (ZTNA)
Protect against supply chain attacks that rely on supplier access to your systems via granular access controls. This cloud-delivered solution validates user identities and device health and compliance before granting access to your resources. It authenticates requests from trusted partners, regardless of their location.
Secure Your Legacy Manufacturing Technology
You need to protect your legacy or unpatched manufacturing control systems and processes from known vulnerabilities. These devices often run out-of-date operating systems or browsers that can't be updated because they are no longer supported – yet they need to be connected to the network.
Firewall and SD-RED can help. Put SD-RED in front of an exposed device, and it tunnels traffic to a protective Firewall for scanning. If your network is flat, you will likely need to make changes to IP address schemes and possible switch topology – and our technical specialists can discuss your situation and show you how to do this.
Protect Your Data Across Your Multi-Cloud Manufacturing Environments
To power up smart factories, drug and device manufacturers are increasingly using cloud platforms and SaaS applications that need to be protected from threats. Cloud Native Security provides complete multi-cloud security coverage across your environments, workloads, and identities.
It protects your cloud infrastructure and data with flexible host and container workload security for Windows and Linux. Multi-layered technologies, including cloud-native behavioral and exploit runtime detections, protect against ransomware and other advanced attacks and identify threats such as container escapes, kernel exploits, and privilege-escalation attempts.
Cybersecurity Solutions for Manufacturing
Cloud Optix: Easily identify cloud resource vulnerabilities, ensure compliance, and respond to threats faster.

Intercept X Endpoint: Intercept X Endpoint delivers unparalleled protection, stopping advanced attacks before they impact your systems. Powerful EDR and XDR tools let your organization hunt for, investigate, and respond to suspicious activity and indicators of attack.
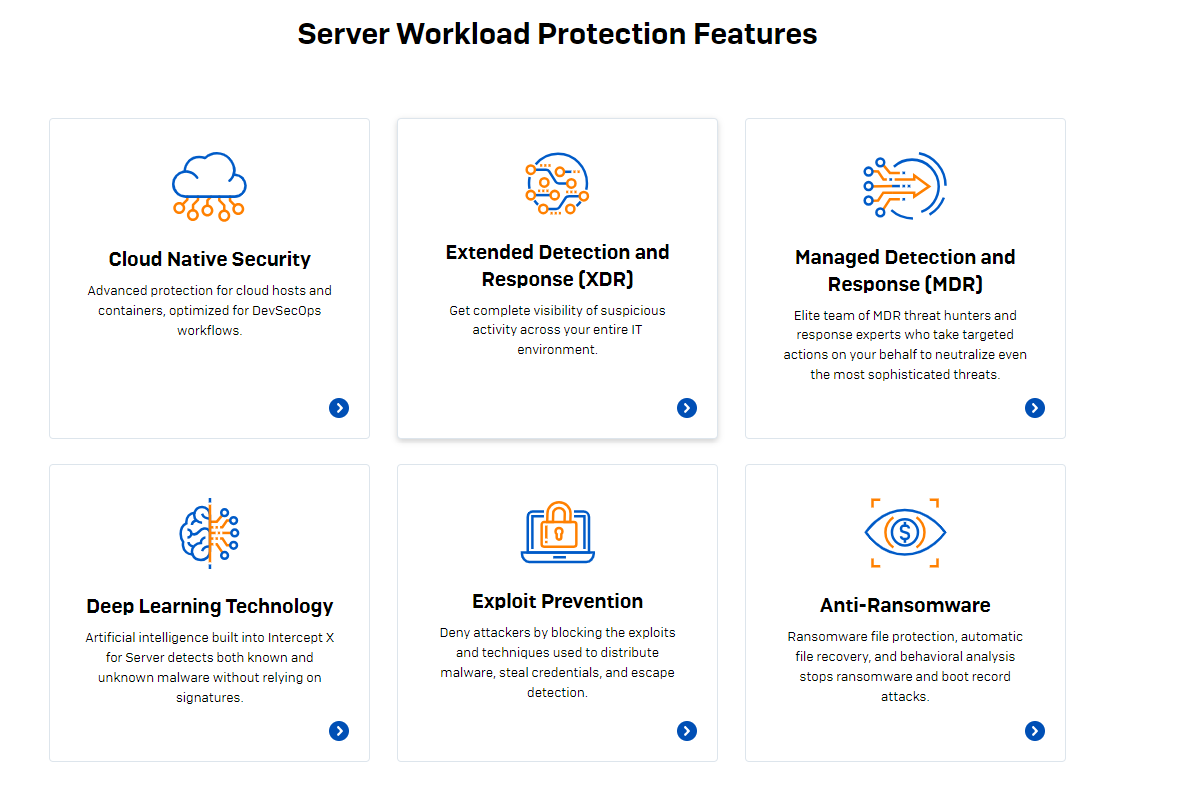
Intercept X for Server: High-impact protection with low impact on performance for on-premise, data center, and cloud workloads.
Synchronized Firewall Security: Your Firewall and Endpoint – Working Together. Firewall is part of the world’s best cybersecurity system, integrating in real time with Central and Intercept X.
XDR: Unified XDR platform enables you to detect, investigate, and respond to multi-stage threats, across all key attack vectors, in the shortest time.
MTR: Get cybersecurity delivered as a service with 24/7 ransomware and breach prevention services.
Microsoft 365 Security: Many cyberattacks start with phishing. Email Security integrates with M365 email in minutes, protecting users faster, unlocking end-to-end visibility across your full M365 suite with XDR.
Compliance Standards
Our ContinuousMTR which is delivered in partnership with Sophos complies with:
GxP - Data Integrity, Cybersecurity, Infrastructure Qualification
HIPAA
PCI DSS
CIS Critical Security Controls
General Data Protection Regulation
Sarbanes-Oxley Act
Children's Internet Protection Act
California Consumer Privacy Act
Australian Signals Directorate
Protection of Personal Information Act
NIST Cybersecurity Framework
NIS Directive
NYDFS Cybersecurity Regulation
ISO/IEC 27001:2022
The Ohio Data Protection Act
NIST SP800-171
NERC CIP
HITRUST Common Security Framework
Achieve Cyber Insurance Requirements with MDR
High levels of cyber control are commonly required by insurance providers as conditions of coverage. Managed Detection and Response (MDR) enables organizations to achieve many of the cyber controls that are key to insurability, including 24/7 Endpoint Detection and Response, web security, logging and monitoring, and more.
ContinuousMTR - Delivered as a Managed Service
In every service we offer, the software app is continuously qualified. Also the customer's instance is continuously validated. In each run, 100% regression is performed.

Conclusion
Industry 4.0 and smart factories are transforming the manufacturing industry, particularly in the drug and device sectors. However, this digital transformation and IT/OT convergence have expanded the attack surface, increasing vulnerabilities to cyberattacks, production sabotage, and IP leakage.
To address these challenges and ensure compliance with FDA Data Integrity mandates, xLM has partnered with Sophos to offer Cybersecurity-as-a-Service.
Key features of the ContinuousMTR Cybersecurity-as-a-Service include:
1. 24/7/365 Managed Detection and Response (MDR)
2. Zero Trust Network Access (ZTNA) for secure access to critical systems
3. Endpoint protection with Intercept X
4. Extended Detection and Response (XDR) for holistic cybersecurity monitoring
5. User-based access controls and risk visibility
6. Data Loss Prevention
7. Supply chain attack mitigation
8. Legacy manufacturing technology protection
9. Multi-cloud environment security
The service is designed to be compatible with existing security investments and can be tailored to specific industry needs. It offers protection against ransomware, data breaches, insider attacks, and supply chain vulnerabilities.
ContinuousMTR complies with various standards, including GxP, HIPAA, PCI DSS, GDPR, and others. It also helps organizations meet cyber insurance requirements by providing high levels of cyber control.
In conclusion, as manufacturing companies embrace digital transformation, robust cybersecurity measures are crucial to protect against evolving threats. The ContinuousMTR Cybersecurity-as-a-Service offers a comprehensive solution that addresses the unique challenges faced by the manufacturing industry, particularly in the life sciences sector.
By implementing this service, companies can reduce their business risk exposure, increase data integrity compliance, and ensure the protection of their critical assets and intellectual property.
xLM in the News
Latest AI News
ContinuousMTR FAQs
Question | Answer |
|---|---|
1. What is ContinuousMTR? | ContinuousMTR is a Cybersecurity-as-a-Service solution specifically designed for drug and device manufacturers. It provides comprehensive protection against a wide range of cyber threats, including ransomware attacks, data breaches, insider threats, and supply chain vulnerabilities. The service is delivered and managed by xLM in partnership with Sophos, leveraging advanced security technologies and 24/7 expert support. |
2. How does ContinuousMTR address the cybersecurity challenges of Industry 4.0 and smart factories? | Industry 4.0 and the adoption of smart factories have expanded the attack surface for manufacturers due to increased digital transformation and IT/OT convergence. This exposes them to higher risks of cyberattacks, production sabotage, and intellectual property theft. ContinuousMTR addresses these challenges through: Managed Detection and Response (MDR): 24/7 monitoring and response to sophisticated cyberattacks. Zero Trust Network Access (ZTNA): Secure access control to critical systems and data, verifying every user and device. Endpoint Protection with Intercept X: Proactive threat detection and prevention using AI and other advanced technologies. Extended Detection and Response (XDR): Comprehensive visibility across the entire security environment for faster threat detection and response. Supply Chain Attack Mitigation: Security measures to protect against vulnerabilities that can infiltrate through third-party suppliers. |
3. What are the key benefits of using ContinuousMTR? | ContinuousMTR offers numerous benefits to drug and device manufacturers, including: Reduced Business Risk Exposure: Minimizes the likelihood and impact of successful cyberattacks. Increased Data Integrity Compliance: Helps meet FDA data integrity mandates and other regulatory requirements. Enhanced Protection for Critical Assets: Safeguards intellectual property, manufacturing processes, and sensitive data. Proactive Threat Detection and Response: Identifies and neutralizes threats before they can cause significant damage. 24/7 Expert Support: Access to a team of cybersecurity specialists who can assist with incident response and other security needs. Compliance with Industry Standards: Aligns with GxP, HIPAA, PCI DSS, GDPR, and other relevant regulations. |
4. How does ContinuousMTR secure access to critical industrial control systems and data? | ContinuousMTR uses a Zero Trust Network Access (ZTNA) approach, which operates on the principle of "trust nothing, verify everything." This means that every user and device attempting to access critical systems and data must be continuously validated. ZTNA ensures that only authorized users and devices with a proven health status can connect, minimizing the risk of unauthorized access and lateral movement of threats. |
5. How does ContinuousMTR protect against insider threats? | ContinuousMTR incorporates features to mitigate insider threats through: User-Based Access and Controls: Granular control over user access to specific resources and data. User Risk Visibility: Identifies and monitors risky users based on behavior patterns and threat history. Data Loss Prevention: Prevents sensitive data from leaving the organization's control, whether intentionally or accidentally. |
6. What role does Intercept X play in ContinuousMTR? | Intercept X is an advanced endpoint protection solution that utilizes deep learning, anti-exploit, anti-ransomware, and malicious traffic detection to proactively defend against a wide range of threats. It constantly learns and improves, providing robust protection for endpoints within the ContinuousMTR framework. |
7. Does ContinuousMTR help with meeting cyber insurance requirements? | Yes, ContinuousMTR helps organizations meet the stringent cyber control requirements often imposed by insurance providers. By providing comprehensive cybersecurity measures such as 24/7 endpoint detection and response, web security, logging and monitoring, ContinuousMTR demonstrates a strong security posture that can satisfy insurance conditions and potentially reduce premiums. |
8. What kind of support is provided with ContinuousMTR? | ContinuousMTR is a fully managed service, meaning that xLM and Sophos provide ongoing support, including: 24/7/365 Security Monitoring and Incident Response: A dedicated team of experts continuously monitors the environment and responds to security events and incidents. Proactive Threat Hunting: Experts actively search for potential threats that may bypass traditional security measures. Security Consulting and Guidance: Assistance with developing and implementing security strategies, policies, and best practices. Software and Infrastructure Management: Continuous updates and maintenance of the security software and infrastructure. |
9. How can I get started with ContinuousMTR? | If you're ready to experience a streamlined, efficient, and compliant managed threat response solution, contact xLM to learn more about ContinuousMTR and how it can benefit your organization. |

